Verifying digital signatures: Decred
The verification of digital signatures ensures that a message wasn’t altered and that the sender is the one who ‘signed’ the message, the owner of the key pair.
By Marcelo Martins - March 28, 2019
Don’t install or use software without first verifying its digital signature.
1. Introduction Permalink
The verification of digital signatures ensures that a message wasn’t altered and that the sender is the one who ‘signed’ the message, the owner of the key pair.
To learn more read Verification of digital signatures.
Learn more about Decred Verifier, a shell script also ported to Python that automates the digital signature and hash verification process.
2. Digital signature: Decred Permalink
2.1. With manifest (indirect) Permalink
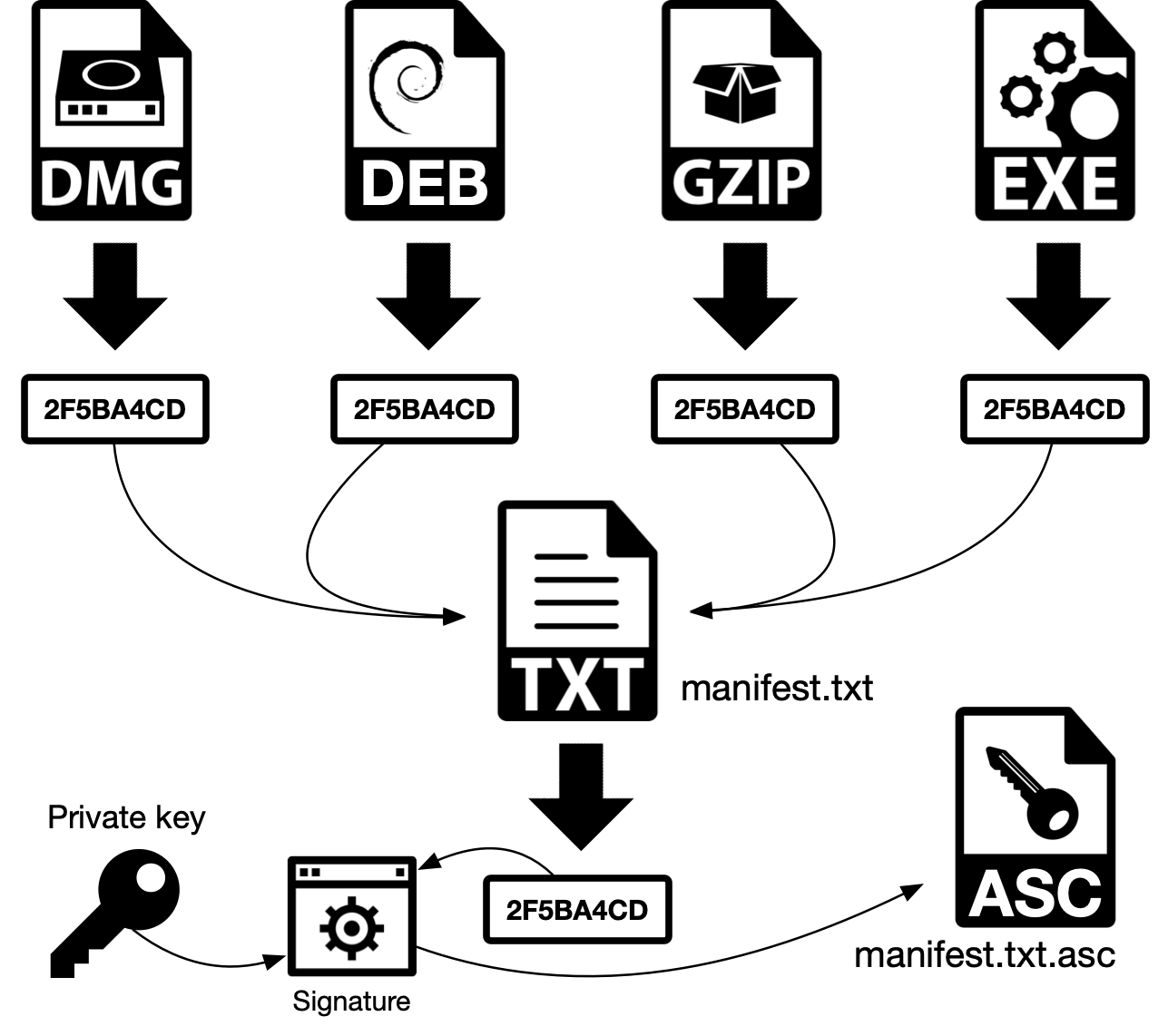
a) The hash (digest) of Decred packages, here represented as package.tar.gz (GZIP, in the schematic) is generated
b) The hash is stored in a text file manifest-decrediton-$VERSION.txt, that contains the name of each file and its corresponding hash
c) The manifest manifest-decrediton-$VERSION.txt is signed (encrypted) with the publisher’s private key. It means that the process will generate a hash for the manifest file and this hash will be encrypted using the publisher’s private key. This encrypted hash will be stored in another file, manifest-decrediton-$VERSION.txt.asc. At the end of the process we have the files package.tar.gz, the manifest manifest-decrediton-$VERSION.txt and the digitally signed manifest manifest-decrediton-$VERSION.txt.asc.
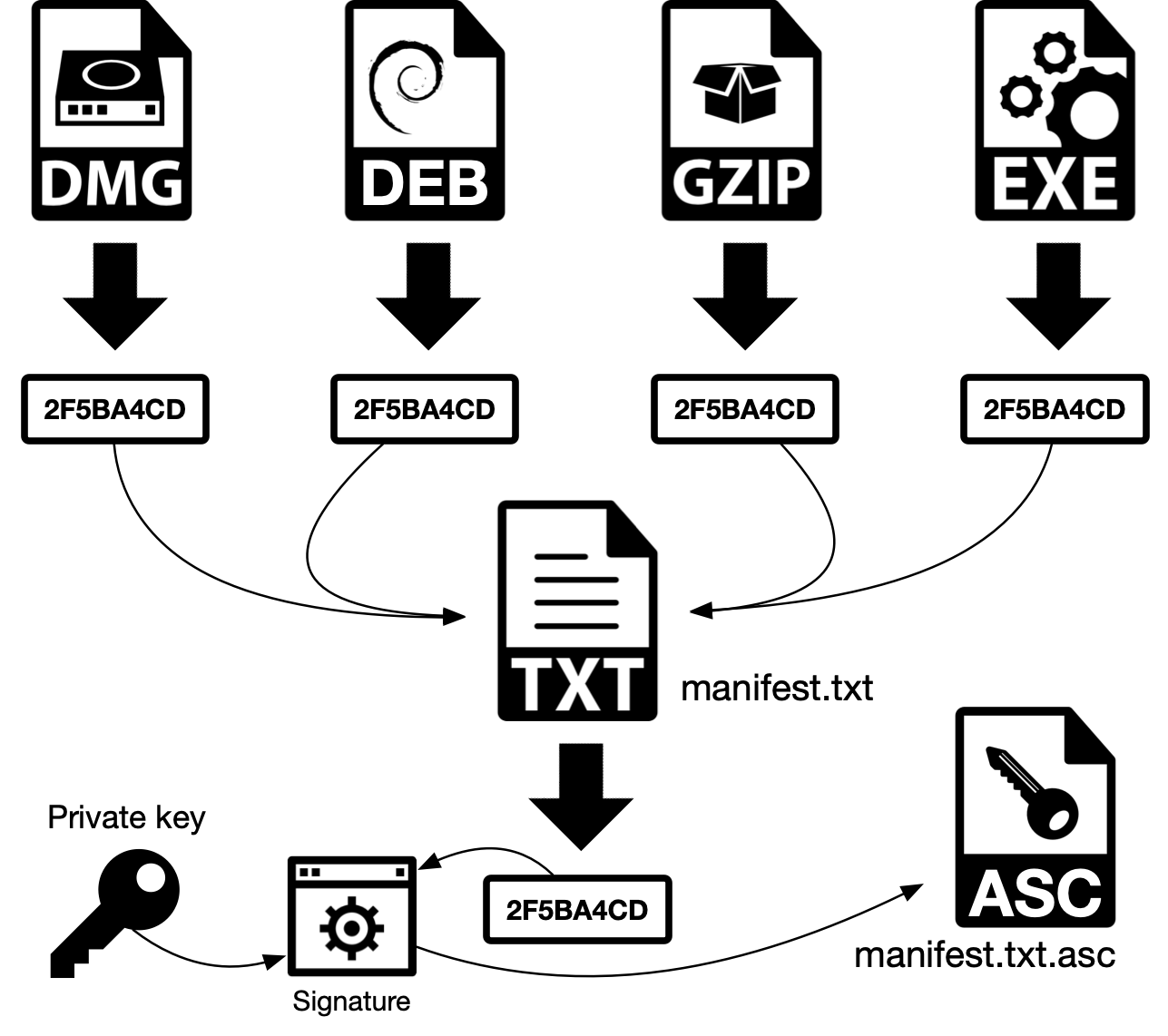
Figure 3 - Digital signature with manifest
2.2. Signature verification Permalink
a) The verification process generates a hash of the manifest manifest-decrediton-$VERSION.txt.
b) The signed hash (encrypted hash) manifest-decrediton-$VERSION.txt.asc is decrypted using the sender’s public key and the original hash is obtained. If both hashes are equal, the message wasn’t altered and the sender is who we think he is, because this public key could not decrypt a hash encrypted with a private key from another pair. In asymmetric cryptography both keys from the same pair are used. The process started with one key and ended with the other one.
c) The user generates a hash of the file package.tar.gz (GZIP, in the schematic) and compares with the hash stores inside the manifest manifest-decrediton-$VERSION.txt. If both hashes are equal, the file wasn’t modified.
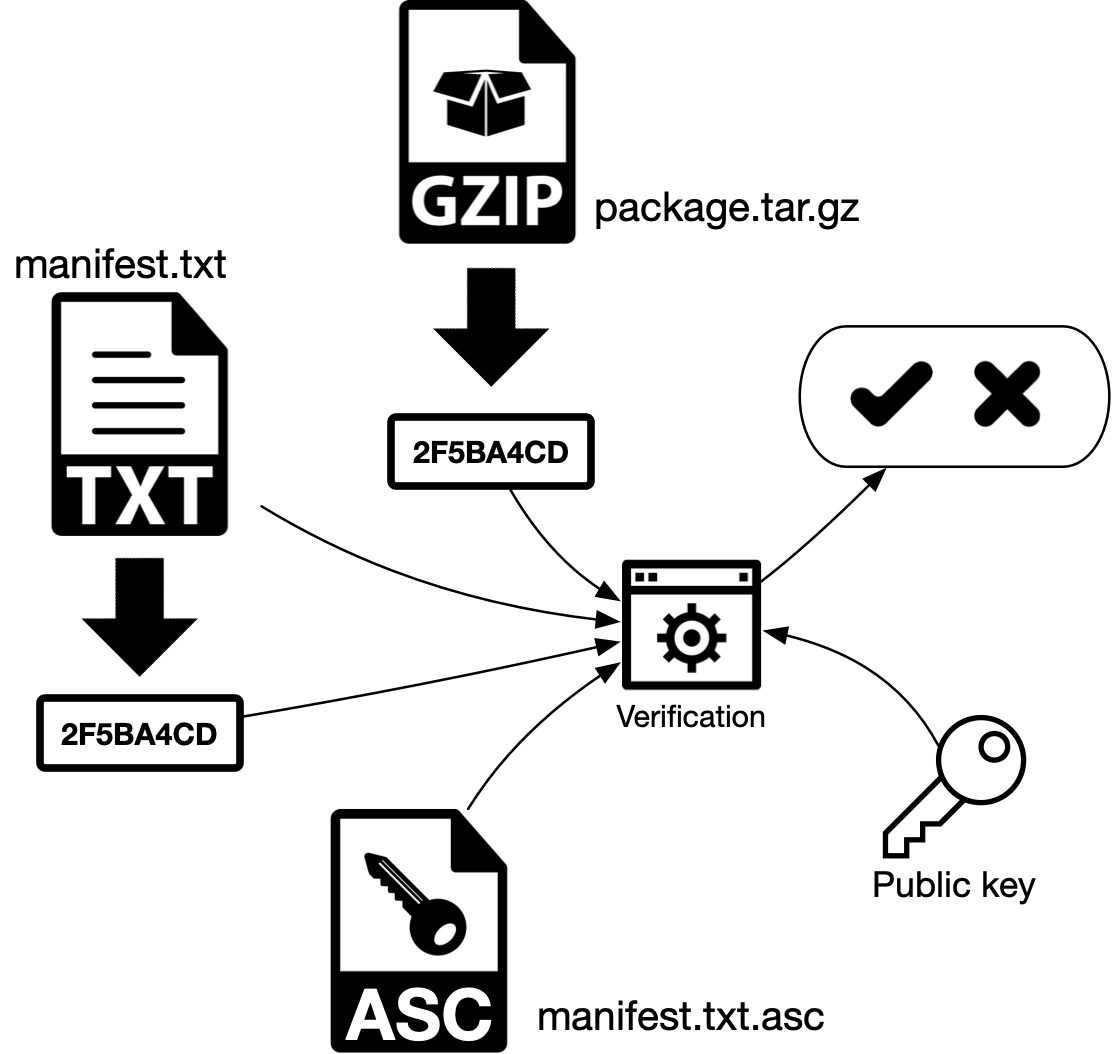
Figure 4 - Digital signature verification with manifest
3. File verification Permalink
Don’t install or use software without first verifying its digital signature.
This section describes the steps to download and verify Decrediton. These steps may be used to verify any other downloaded software from the Internet. The user will have to import the developers’ public key (hopefully all this information will be displayed in the website). Usually public keys are imported once, then again only if the key pair is revoked or replaced.
Learn more about Decred Verifier, a shell script also ported to Python that automates the digital signature and hash verification process.
3.1. Mac Permalink
a) Go to https://github.com/decred/decred-binaries/releases/
b) Download to the same directory the files decrediton-$VERSION.dmg, manifest-decrediton-$VERSION.txt and manifest-decrediton-$VERSION.txt.asc
c) In case the key hasn’t already been imported (error: ‘gpg: Can’t check signature: No public key’): import the developer’s public key (GPG will try to connect to the Internet using port TCP/11371):
$ gpg --keyserver pgp.mit.edu --recv-keys 0x518A031D
d) Make sure the correct key was imported:
gpg: key 6DF634AA7608AF04: public key "Decred Release <release@decred.org>" imported
e) Verify the digital signature:
$ gpg --verify manifest-decrediton-$VERSION.txt.asc
gpg: assuming signed data in 'manifest-decrediton-v1.1.3.txt'
gpg: Signature made Thu Dec 21 17:15:58 2017 WET
gpg: using RSA key 6D897EDF518A031D
gpg: Good signature from "Decred Release <release@decred.org>" [unknown]
gpg: WARNING: This key is not certified with a trusted signature!
gpg: There is no indication that the signature belongs to the owner.
Primary key fingerprint: FD13 B683 5E24 8FAF 4BD1 838D 6DF6 34AA 7608 AF04
Subkey fingerprint: F516 ADB7 A069 852C 7C28 A02D 6D89 7EDF 518A 031D
f) Look in the gpg output for: “using RSA key 6D897EDF518A031D” (only when verifying for the first time after importing the key). Notice that the second half of the RSA key, shown in the third line above, is shown in step c) and also the text ‘Good signature from “Decred Release”’
g) To generate the hash and manually compare it with the hashes inside manifest-decrediton-$VERSION.txt:
$ shasum -a 256 decrediton-$VERSION.dmg
$ cat manifest-decrediton-$VERSION.txt
To automate the process and execute a one-liner:
$ grep `shasum -a 256 decrediton-$VERSION.dmg` manifest-decrediton-$VERSION.txt
If the command above returns nothing it means the hash wasn’t found in the manifest and this is a problem.
h) Mount the DMG image and copy the new Decrediton app to the Applications folder.
Reference: https://docs.decred.org/advanced/verifying-binaries/
Obs.: If you don’t have gpg, go to https://gpgtools.org/
Web of Trust Permalink
The warning shown in step e) above with a message about the key not being certified with a trusted signature is related to PGP Web of Trust. In a decentralized model there is no central authority like the Certification Authority in PKI that can tell if a key belongs to one specific user (identity validation). So the web of trust works by verifying if a key is ‘signed’ by other key (user) trusted by the system, creating a web of trust. Considering I don’t trust any key that could have signed Decred developers’ public key, this warning was already expected.
4.2. Debian Permalink
a) Go to https://github.com/decred/decred-binaries/releases/
b) Download to the same directory the files decrediton-$VERSION.deb, manifest-decrediton-$VERSION.txt and manifest-decrediton-$VERSION.txt.asc
c) In case the key hasn’t already been imported (error: ‘gpg: Can’t check signature: No public key’): import the developer’s public key (GPG will try to connect to the Internet using port TCP/11371):
$ gpg --keyserver pgp.mit.edu --recv-keys 0x518A031D
In case of error ‘gpg: keyserver receive failed: No dirmngr’:
$ sudo apt-get install dirmngr
d) Make sure the correct key was imported:
gpg: key 6DF634AA7608AF04: public key "Decred Release <release@decred.org>" imported
e) Verify the digital signature:
$ gpg --verify manifest-decrediton-$VERSION.txt.asc
gpg: assuming signed data in 'manifest-decrediton-v1.1.3.txt'
gpg: Signature made Thu Dec 21 17:15:58 2017 WET
gpg: using RSA key 6D897EDF518A031D
gpg: Good signature from "Decred Release <release@decred.org>" [unknown]
gpg: WARNING: This key is not certified with a trusted signature!
gpg: There is no indication that the signature belongs to the owner.
Primary key fingerprint: FD13 B683 5E24 8FAF 4BD1 838D 6DF6 34AA 7608 AF04
Subkey fingerprint: F516 ADB7 A069 852C 7C28 A02D 6D89 7EDF 518A 031D
f) Look in the gpg output for: “using RSA key 6D897EDF518A031D” (only when verifying for the first time after importing the key). Notice that the second half of the RSA key, shown in the third line above, is shown in step c) and also the text ‘Good signature from “Decred Release”’
g) To generate the hash and manually compare it with the hashes inside manifest-decrediton-$VERSION.txt:
$ sha256sum decrediton_$VERSION.deb
$ cat manifest-decrediton-$VERSION.txt
To automate the process and execute a one-liner:
$ grep `sha256sum decrediton-$VERSION.deb` manifest-decrediton-$VERSION.txt
If the command above returns nothing it means the hash wasn’t found in the manifest it means that the file may have been modified after its creation.
h) Install with command:
$ dpkg -i decrediton-$VERSION.deb
Warning in GPG output: Read more about Web of Trust in section 3.1.
Reference: https://docs.decred.org/advanced/verifying-binaries/
Obs.: If you don’t have gpg, go to https://gpgtools.org/
4.3. Other Linux flavors (and also on Debian) Permalink
a) Go to https://github.com/decred/decred-binaries/releases/
b) Download to the same directory the files decrediton-$VERSION.tar.gz, manifest-decrediton-$VERSION.txt and manifest-decrediton-$VERSION.txt.asc
c) In case the key hasn’t already been imported (error: ‘gpg: Can’t check signature: No public key’): import the developer’s public key (GPG will try to connect to the Internet using port TCP/11371):
$ gpg --keyserver pgp.mit.edu --recv-keys 0x518A031D
In case of error ‘gpg: keyserver receive failed: No dirmngr’:
$ sudo apt-get install dirmngr
d) Make sure the correct key was imported:
gpg: key 6DF634AA7608AF04: public key "Decred Release <release@decred.org>" imported
marcelo@fullnode:~/Downloads$ gpg --keyserver pgp.mit.edu --recv-keys 0x518A031D
gpg: key 6DF634AA7608AF04: public key "Decred Release <release@decred.org>" imported
gpg: Total number processed: 1
gpg: imported: 1
e) Verify the digital signature:
$ gpg --verify manifest-decrediton-$VERSION.txt.asc
gpg: assuming signed data in 'manifest-decrediton-v1.1.3.txt'
gpg: Signature made Thu Dec 21 17:15:58 2017 WET
gpg: using RSA key 6D897EDF518A031D
gpg: Good signature from "Decred Release <release@decred.org>" [unknown]
gpg: WARNING: This key is not certified with a trusted signature!
gpg: There is no indication that the signature belongs to the owner.
Primary key fingerprint: FD13 B683 5E24 8FAF 4BD1 838D 6DF6 34AA 7608 AF04
Subkey fingerprint: F516 ADB7 A069 852C 7C28 A02D 6D89 7EDF 518A 031D
f) Look in the gpg output for: “using RSA key 6D897EDF518A031D” (only when verifying for the first time after importing the key). Notice that the second half of the RSA key, shown in the third line above, is shown in step c) and also the text ‘Good signature from “Decred Release”’
g) To generate the hash and manually compare it with the hashes inside manifest-decrediton-$VERSION.txt:
$ sha256sum decrediton-$VERSION.tar.gz
$ cat manifest-decrediton-$VERSION.txt
To automate the process and execute a one-liner:
$ grep `sha256sum decrediton-$VERSION.tar.gz` manifest-decrediton-$VERSION.txt
If the command above returns nothing it means the hash wasn’t found in the manifest it means that the file may have been modified after its creation.
h) There is nothing to install. Extract; enter the directory; execute:
$ tar -xvzf decrediton-$VERSION.tar.gz
$ cd decrediton-$VERSION
$ ./decrediton
Warning in GPG output: Read more about Web of Trust in section 3.1.
Reference: https://docs.decred.org/advanced/verifying-binaries/
Obs.: If you don’t have gpg, go to https://gpgtools.org/
4.4. Windows Permalink
a) Go to https://github.com/decred/decred-binaries/releases/
b) Download to the same directory the files decrediton-$VERSION.exe, manifest-decrediton-$VERSION.txt and manifest-decrediton-$VERSION.txt.asc
c) In case the key hasn’t already been imported (error: ‘gpg: Can’t check signature: No public key’): import the developer’s public key (GPG will try to connect to the Internet using port TCP/11371):
> gpg --keyserver pgp.mit.edu --recv-keys 0x518A031D
d) Make sure the correct key was imported:
gpg: key 6DF634AA7608AF04: public key "Decred Release <release@decred.org>" imported
e) Verify the digital signature:
> gpg --verify manifest-decrediton-$VERSION.txt.asc
gpg: assuming signed data in 'manifest-decrediton-v1.1.3.txt'
gpg: Signature made Thu Dec 21 17:15:58 2017 WET
gpg: using RSA key 6D897EDF518A031D
gpg: Good signature from "Decred Release <release@decred.org>" [unknown]
gpg: WARNING: This key is not certified with a trusted signature!
gpg: There is no indication that the signature belongs to the owner.
Primary key fingerprint: FD13 B683 5E24 8FAF 4BD1 838D 6DF6 34AA 7608 AF04
Subkey fingerprint: F516 ADB7 A069 852C 7C28 A02D 6D89 7EDF 518A 031D
f) Look in the gpg output for: “using RSA key 6D897EDF518A031D” (only when verifying for the first time after importing the key). Notice that the second half of the RSA key, shown in the third line above, is shown in step c) and also the text ‘Good signature from “Decred Release”’
g) Windows doesn’t come with a native tool to generate SHA256 hashes. Windows users may try the tool PowerShell File Checksum Integrity Verifier (PsFCIV) available at Microsoft Technet.
Warning in GPG output: Read more about Web of Trust in section 3.1.
Reference: https://docs.decred.org/advanced/verifying-binaries/
Obs.: If you don’t have gpg, go to https://gpgtools.org/





Comments ()